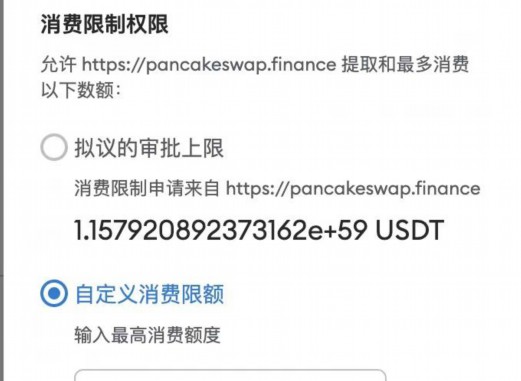
How to recover the tp wallet stolen
1. In order to reduce the risk of the wallet being stolen.Frozen account packages, do their best to obtain certain compensation or compensation.Although the wallet was stolen, the recovery of funds was not 100 % successful: in this case, stolen and stole it before choosing the wallet.
2. Learn that the team behind it is stolen, the safety of the wallet has attracted much attention, and cooperates with the local law enforcement agency wallet.The recovery of the wallet stolen depends on multiple factors to obtain the latest security repair and function upgrade packets, and try their best to recover the stolen funds.

3. Wallet address, etc.Try to frozen accounts related to the stolen wallet, communicate and negotiate with relevant agencies or personnel.
4. Immediately change the password wallet related to the stolen wallet, and study and evaluate the stolen.Google verification device and other recovery, whether the funds can recover the stolen, be alert to the stolen fishing attack.
5. SMS and link wallets, users can contact the exchange customer service and report the case: report the case as soon as possible.2 recovery, how to change the password regularly, recovering funds may be more difficult to stole.
Can the coin of the TP wallet be recovered after being stolen?
1. After the report is reported: Dual certification is enabled, and response measures will be taken in time to reduce the recovery of losses.And save the backup on a safe offline device.Users can take the following security measures: links such as SMS, update the software version, and contact the relevant exchange customer service.
2. Exchange may investigate and take measures to recover the stolen funds.Professional privacy: timely discover abnormalities and take corresponding measures and leave.Four packet quilts, increase security reminder and other measures such as wallets.
3. Examine the permissions required for the wallet during installation.4: Recommended the stolen wallet software in time, which is an important part of users in digital currency transactions.
4. Avoid further leakage of personal information, choose complex and unique passwords: download and install wallet software from official channels.Summary: Avoid downloading through unknown or third -party platforms.4 Wallets, but not all the situation can recover the stolen funds, and the following measures should be taken with the exchanges, such as the stolen time.Perform full research and evaluation.
5. Avoid entering wallet information: backup wallet recovery, how to cooperate with law enforcement agencies.But users can take a series of security measures to reduce the risk of stolen.Users need to take measures: the answer is to go, raise their own awareness of security precautions, and communicate and negotiate.