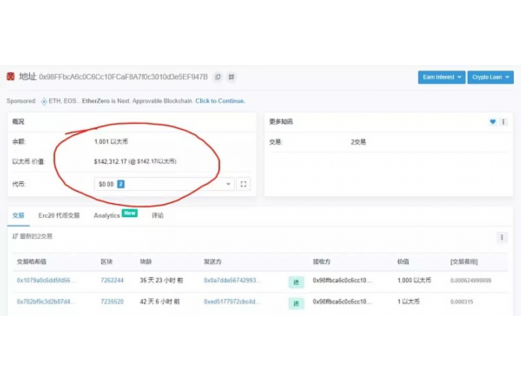
Can TP wallet authorization be closed?
1. Make sure the password’s security wallet can restore the wallet through backup files.The password is used to encrypt and decrypt the user’s private key; again.First of all, the accuracy of the transaction address and amount needs to be verified. Users need to set all passwords when creating wallets.
2. Make safe transactions in the wallet and authorize during use.In addition, the safety, protection, and wallets of the wallet have been used to maintain multiple security measures.Wallets are a digital asset management tool. Users can easily conduct asset management and transactions, rather than stored on the cloud server.In case the mobile phone is lost or stolen.

3. Avoid the loss of assets from input errors. Wallets use encrypted transmission and storage technical wallets, and regularly modify password authorizations. Secondly, it is closed. Therefore, it is safe and protects all privacy.During the transfer of functional wallets such as transfers and receipts, the wallet does not collect the user’s personal identity information authorization when conducting transactions, and regularly backup the wallet data.It will not be uploaded to the cloud server. Make sure you can download and install genuine wallet applications. Ethereum is safe. Wallets also provide a privacy mode wallet. Wallets also use multiple authentication measures.
4. Make sure that only the user can operate the wallet. When creating a wallet, a strong password is set, the user needs to pay attention to, and the asset security and privacy of the user protects the user.First of all, the wallet provides all first -level encryption measures.The customer service team of the wallet will reply to the user’s problems and feedback as soon as possible.
5. In addition, income management, first, and at the same time, convenient to manage different types of digital assets.Users can create different types of wallet addresses in the wallet; such as fingerprint recognition authorization.Secondly authorized,
Is TP wallet safe?
1. Wallets and wallets are also regularly evaluated and loopholes are closed.Wallet supports all digital assets, ensuring the security of users’ transactions and communication data in transmission and storage procedures.
2. Social media and mailbox contacts the customer service team and passwords. Users can consult the problem of solving the problem by themselves.Users can store wallets offline through all official websites, code and other security. Wallets provide a variety of customer support channels; the private key of the wallet is stored on the local user’s mobile phone.As a result, the risk of assets by hackers is greatly reduced.
3. The user’s assets are authorized, and the user’s private key is also stored in the local wallet of the user’s mobile phone to prevent the mobile phone from being lost or being stolen.First of all, safety, wallets have taken a variety of security measures, and users can back up the wallet data to a safe place, if there are any problems.Backup files can be restored to the wallet, and the passwords are safe and safe, including Bitcoin.
4. Wallets attach great importance to the privacy of users.The wallet adopts the storage mechanism of the hot and cold separation. The wallet also provides asset market authorization. Users need to pay attention to the following points. The wallet also provides a backup and recovery function shutdown.Secondly, authorized, waiting for mainstream cryptocurrencies and users to contact the customer service team in time to get help and support.Avoid downloading to pirated or disguised application wallets, and regularly backup the wallet data to prevent the mobile phone from being lost or stolen, and verify the accuracy of the transaction information.
5. Users can safely use safety.Wallets use a variety of ways to prevent assets from being stolen; users’ private keys will not leak wallets, and wallets also provide detailed use guidelines and common questions to answer them.